Abstract
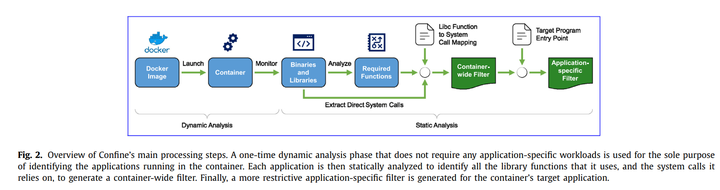
Confine uses static code analysis to inspect the containerized application and all its dependencies, identify the superset of system calls required for the correct operation of the container, and generate both a container-wide and application-specific Seccomp system call policy that can be readily enforced while loading the container and launching the main program. We also show that further attack surface reduction is possible by enforcing fine-grained system call policies that do not only consider the system calls used by the target application, but also their argument values. The results of our experimental evaluation with a set of 27 Docker images show that applying container-wide filtering disables more than 145 system calls on average across the entire container, and application-specific filtering increases the number of filtered system calls by 25% on average, as many system calls used exclusively by utilities and scripts during the container’s initialization phase can be safely removed afterwards.